(Reproduced Rachna Khaira Tribune News Service report )
It was only last November that the UIDAI asserted that “Aadhaar data is fully safe and secure and there has been no data leak or breach at UIDAI.”
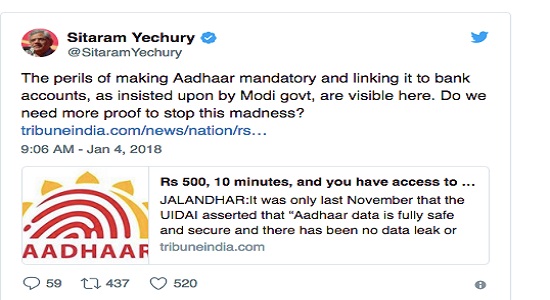
Today, The Tribune “purchased” a service being offered by anonymous sellers over WhatsApp that provided unrestricted access to details for any of the more than 1 billion Aadhaar numbers created in India thus far.
It took just Rs 500, paid through Paytm, and 10 minutes in which an “agent” of the group running the racket created a “gateway” for this correspondent and gave a login ID and password. Lo and behold, you could enter any Aadhaar number in the portal, and instantly get all particulars that an individual may have submitted to the UIDAI (Unique Identification Authority of India), including name, address, postal code (PIN), photo, phone number and email.
What is more, The Tribune team paid another Rs 300, for which the agent provided “software” that could facilitate the printing of the Aadhaar card after entering the Aadhaar number of any individual.
When contacted, UIDAI officials in Chandigarh expressed shock over the full data being accessed, and admitted it seemed to be a major national security breach. They immediately took up the matter with the UIDAI technical consultants in Bangaluru.
Sanjay Jindal, Additional Director-General, UIDAI Regional Centre, Chandigarh, accepting that this was a lapse, told The Tribune: “Except the Director-General and I, no third person in Punjab should have a login access to our official portal. Anyone else having access is illegal, and is a major national security breach.”
Investigations by The Tribune reveal that the racket may have started around six months ago, when some anonymous groups were created on WhatsApp. These groups targeted over 3 lakh village-level enterprise (VLE) operators hired by the Ministry of Electronics and Information Technology (ME&IT) under the Common Service Centres Scheme (CSCS) across India, offering them access to UIDAI data.
CSCS operators, who were initially entrusted with the task of making Aadhaar cards across India, were rendered idle after the job was withdrawn from them. The service was restricted to post offices and designated banks to avoid any security breach in November last year.
Spotting an opportunity to make a quick buck, more than one lakh VLEs are now suspected to have gained this illegal access to UIDAI data to provide “Aadhaar services” to common people for a charge, including the printing of Aadhaar cards.
However, in wrong hands, this access could provide an opportunity for gross misuse of the data. The hackers seemed to have gained access to the website of the Government of Rajasthan, as the “software” provided access to “aadhaar.rajasthan.gov.in”, through which one could access and print Aadhaar cards of any Indian citizen.
However, it could not be ascertained whether the “portals” were genuinely of Rajasthan, or it was mentioned just to mislead. Sanjay Jindal said all of this could be confirmed only after a technical investigation was conducted by the UIDAI.
“Leakage of Aadhaar data reveals that the project has failed the privacy test. At the recently concluded 11th WTO Ministerial Conference, India submitted a written position on e-commerce, opposing the demand for negotiations on e-commerce by the US and its allies. The latter were demanding access to citizens’ database for free.
The revelation by The Tribune also means that the proposed data protection law will now hold no purpose, as the data has already been breached. The state governments must immediately disassociate themselves and cancel the MoU signed with UIDAI,” said Gopal Krishan, New Delhi-based convener of the Citizens Forum for Civil Liberties, who appeared before the Special Parliamentary Committee that examined the Aadhaar Bill in 2010.
A quick chat, and full access
12:30 pm: This correspondent posing as ‘Anamika’ contacted a person on WhatsApp number 7610063464, who introduced himself as ‘Anil Kumar’. He was asked to create an access portal. 12:32pm: Kumar asked for a name, email ID and mobile number, and also asked for Rs 500 to be credited in his Paytm No. 7610063464. 12:35 pm: This correspondent created an email ID, aadharjalandhar@gmail.com, and sent mobile number ******5852 to the anonymous agent. 12:48 pm: Rs 500 transferred through Paytm. 12:49 pm: This correspondent received an email saying, “You have been enrolled as Enrolment Agency Administrator for ‘CSC SPV’. Your Enrolment Agency Administrator ID is ‘Anamika_6677’.” Also, it was said that a password would be sent in a separate mail, which followed shortly.12:50 pm: This correspondent had access to the Aadhaar details of every Indian citizen registered with the UIDAI.
This correspondent later again approached Anil Kumar to ask for software to print Aadhaar cards. He asked for Rs 300 through Paytm No. 8107888008 (in the name of ‘Raj’). Once paid, a person identifying himself as Sunil Kumar called from mobile number 7976243548, and installed software on this correspondent’s computer by accessing it remotely through “TeamViewer”. Once the job was done, he deleted the software drivers, even from the recycle bin.